In this data-centric age, cloud security stands as the linchpin safeguarding the integrity of your cloud computing and infrastructure. As we navigate the ever-shifting landscape of cyber threats, cloud security tools have become essential gatekeepers, providing robust protection for your cloud-based assets.
Here’s a snapshot of key statistics and insights that set the stage for our exploration:
Statistics:
- Cloud-based cyber threats continue to rise, with a 30% increase in cloud security incidents reported in the last year alone.
- By 2024, it’s estimated that nearly 95% of all data breaches will occur in the cloud, making robust security tools paramount.
- The adoption of multi-cloud environments is on the rise, with 79% of organizations using more than one cloud provider. However, this has led to increased complexity in managing cloud data, with 55% finding it more complex than on-premises data management.
What to Expect:
- In this article, we’ll break down the top 15 cloud based security tools that offer unparalleled protection against cyber threats.
- Gain insights into the statistics that underscore the urgency of robust cloud security.
- We’ll use clear, concise language to demystify complex security concepts.
- Discover relevant keywords and entities related to cloud security that are vital in today’s digital landscape.
Now, let’s dive into the world of cloud security and unveil the top 15 tools that promise to fortify your cloud infrastructure against the relentless tide of cyber threats.
What is a Cloud Security Tool?
A Cloud Security Tool is software or a solution designed to protect data, applications, and infrastructure in cloud computing environments.
These tools help safeguard sensitive information, detect and respond to security threats, and ensure compliance with security regulations in cloud-based systems.
They play a critical role in maintaining the confidentiality, integrity, and availability of data stored and processed in the cloud. Cloud Security Tools encompass a wide range of functionalities, including encryption, identity and access management, threat detection, and security monitoring, all aimed at fortifying cloud-based resources against cyber threats and vulnerabilities.
These cloud security monitoring tools are essential for organizations and businesses operating in the cloud to mitigate risks and ensure a secure and compliant cloud computing environment.
Things To Consider While Choosing Cloud Security Tools
Here are three important aspects to take into consideration when implementing a cloud security solution for IT teams managing the cloud migration.
1. Flexibility And Scalability
Scalability for cloud access security brokers (CASB) and customers is made possible through resource sharing, allowing them to add or remove computing, storage, networking, and other assets as necessary. This helps IT in streamlining workloads hosted in the cloud and preventing end-user bottlenecks.
2. Extensive Network Access
The cloud’s ubiquity plays a significant role in its usefulness. With an internet connection, data can be retrieved and uploaded from any location. Cloud security management tools providers keep an eye on and guarantee several metrics, such as latency, access time, etc., that represent how users access cloud services to maintain that wide network access.
3. Security
Cloud security solutions vendors are more prepared to manage threats than the majority of internal IT teams because they work with some of the greatest security specialists in the world. In reality, cloud based security solutions are assets, according to some of the greatest financial institutions in the world and the top managed cloud service providers use the shared-responsibility paradigm.

Unlock Your Potential with Our Cutting-Edge Services!
Experience seamless innovation and transformation with our comprehensive range of services tailored to elevate your business to new heights.
15 Best Cloud Security Tools
The following are the 10 best cloud security tools to use.
1. Zerospam
Zerospam, a cloud-based email security application, protects users from dangerslike spam, malware, phishing, DoS attacks, and other email-related risks.
Pros
- Excellent support team
- Easy to use
- Smart and quick integrations
Cons
- Inadequate maintenance.
- Expensive
Pricing
- Zerospam offers four different subscription options;
- Free
- Premium – $9.99/month
- Business – $39.99/month
- Unlimited – $99.99/month
Additionally offered for Premium and Business are annual plans.
2. Barracuda CloudGen Firewall
Barracuda CloudGen, a SaaS cloud security tool, is a next-generation set of physical, virtual, and cloud-based tools designed to safeguard and improve the functionality of a distributed network infrastructure.
Pros
- Easy to use
- Built-in cloud firewalls and intrusion detection/prevention systems (IDS/IPS)
- Highly customizable admin dashboard
Cons
- Suited more for enterprises
- No free trial
Pricing
- Least expensive appliance costs $68
- Most expensive equipment costs over $100,000
3. Crowdstrike Falcon
Crowdstrike Falcon provides cloud-native full-stack security. It is a cloud security software for cloud encryption tools that leverage cloud-scale AI to lighten the load on security teams and guard against cloud intrusions.
Pros
- Impressive UI
- Multifunctional dashboard
- Responsive support team
Cons
- Expensive
- Utilizes a large amount of bandwidth
Pricing
- 15 days free trial
- Pro – $8.99/month
- Enterprise – $15.99/month
- Elite (call for more information on pricing)
4. Datadog Cloud Security Management
Datadog cloud security provides a cloud workload security system and a cloud security posture management service. It also provides cloud security information and event management (SIEM) tools.
Pros
- Activation of integration at one click
- Avoid and scout for attacks
- Allows for cooperative remediation
Cons
- JSON parsing on logs
Pricing
- Free monitoring for 5 or 10 containers for each host license
- Each additional containers cost $0.002/hr
5. Splunk Enterprise Security
One of the top cloud governance security tools is Splunk Enterprise Security, which offers user-friendly dashboard, anomaly detection, and security investigations in real-time. Its operational intelligence platform’s search and correlation capabilities allow users to gather, monitor, and report from security devices.
Pros
- Continuous security monitoring
- Quick threat investigation
- Scalable and open
Cons
- Expensive
- Steep learning curve
Pricing
Con:
- 60-day free trial
- Light – $83/month
- Enterprise – $173/month
6. Bitglass: Total Cloud Security

BitGlass is one of the more recent cloud security solutions that help users in managing and protect cloud frameworks from dangers posed by both common and Zero-Day malware as well as data leaks.
Pros
- Notify the administrator of multiple or concurrent logins from various geographical locations.
Cons
- Needs improvement with some IDP providers.
Pricing
- Active Platform – $15/month
- Discovery – $8/month for each user.
7. CloudKnox
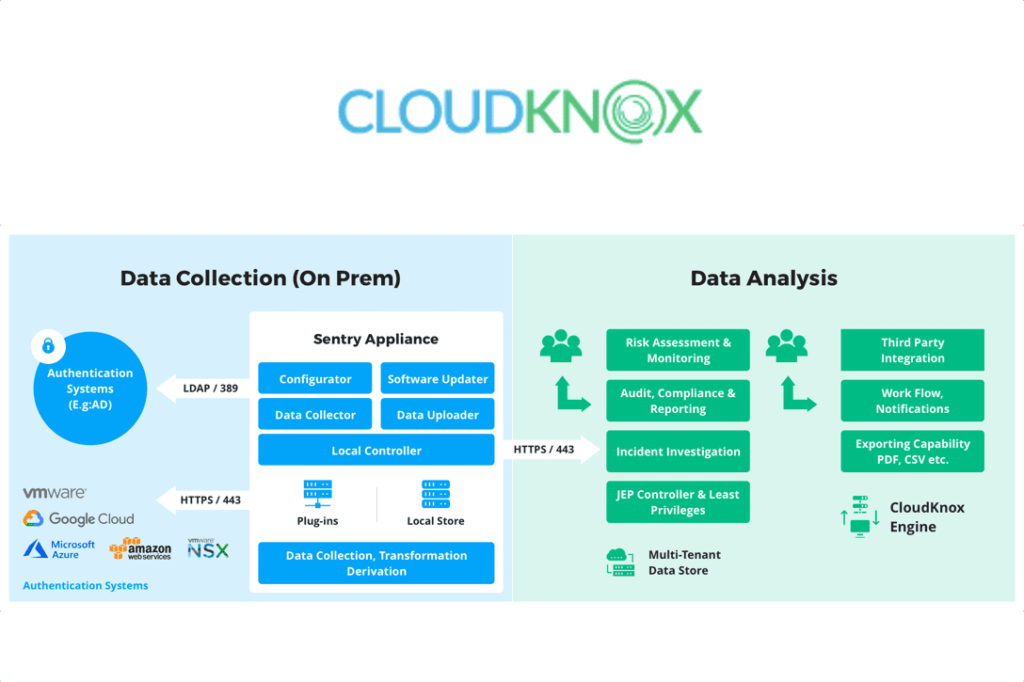
CloudKNox is one of the best Cloud identity and access management (IAM) tools. It provides cloud monitoring, including real-time reporting of unusual activities, management of least-privilege access rules, and handling of exceptions for one-time access.
Pros
- Adaptive risk-based decision making
- Offers a multi-dimensional view of the risk
Cons
- Excessive data access
Pricing
- Contact the firm to learn about pricing
8. Cyscale
Cloud asset mapping company Cyscale also gives evaluations on the security of their operational procedures. This SaaS platform assesses virtualization, databases, microservices, APIs, and frameworks with other cloud platforms.
Pros
- Discovering and mapping cloud assets
- GDPR, HIPAA, PCI-DSS, ISO 27001, and NIST compliance
- CI/CD pipeline testing integration
Cons
- No on-premises version
Pricing
- 14-day free trial
- Custom pricing plan based on per feature
9. Delinea
The current version of Delinea helps to thwart assaults on cloud infrastructures that seek to elevate their privileges. It is a cloud-based software package that offers Privilege Access Management (PAM) services.
Pros
- Improved authentication security
- Multiple integration options
- One window workflow management
Cons
- Works with selected Linux distributions
- Poor documentation
Pricing
- 30-day free trial
- Request custom quote for paid plans.
10. Orca Security
Orca security is one of the best cloud based security tools, which incorporates vulnerability management, multi-cloud compliance and posture management, container security, and other capabilities into a cloud infrastructure, is far more effective and stands among top cloud security tools.
Pros
- Agile risk-covering tool
- Easy setup
- Reduced false positives.
Cons
- Slow UI
- Poor documentation
- No real-time scanning and xDR capabilities.
Pricing
- 30-day free trial
- Request custom quote for paid plans.
11. HashiCorp Vault
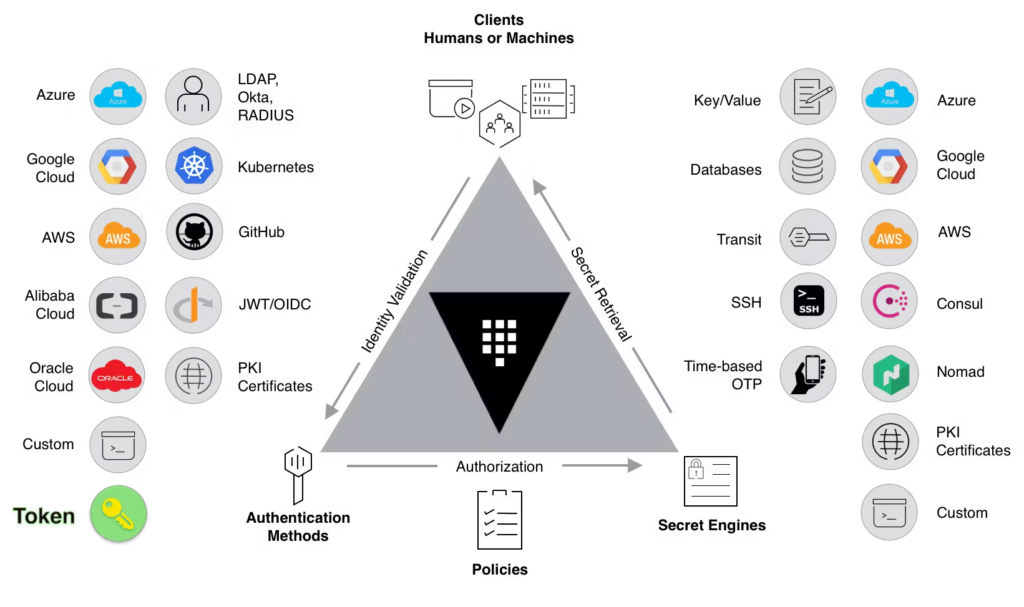
HashiCorp Vault is a versatile tool designed for managing secrets and safeguarding sensitive data within dynamic cloud environments, including AWS. It offers a range of security features, including encryption, access control, and comprehensive secret management capabilities.
Pros:
- Strong encryption for sensitive data protection.
- Robust access control to manage who can access secrets.
- Versatile secret management features for dynamic cloud environments.
Cons:
- Requires configuration and setup, which may have a learning curve.
- May require additional integrations for specific use cases.
Pricing: HashiCorp Vault offers both open-source and enterprise versions. Pricing for the enterprise version is available on request.
12. Trend Micro Cloud One
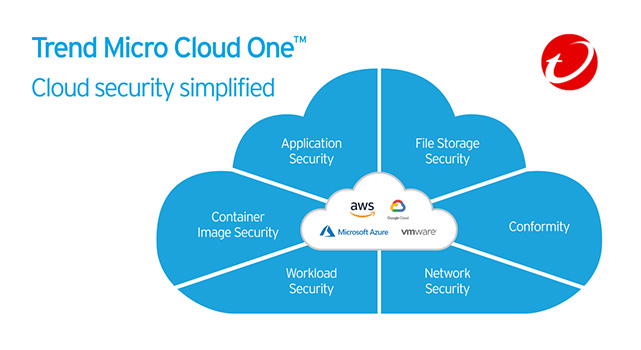
Trend Micro Cloud One is a comprehensive cloud security solution tailored for AWS environments. It provides protection for workloads, containers, and network resources, enhancing the security posture of cloud infrastructure.
Pros:
- Offers extensive cloud security features for AWS.
- Protects workloads and containers.
- Enhances network security within AWS environments.
Cons:
- Some users may find it complex due to the range of features.
- Pricing can be on the higher side for smaller organizations.
Pricing: Trend Micro Cloud One pricing varies based on the specific services and features required. Detailed pricing information can be obtained from Trend Micro.
13. Palo Alto Networks Prisma Cloud
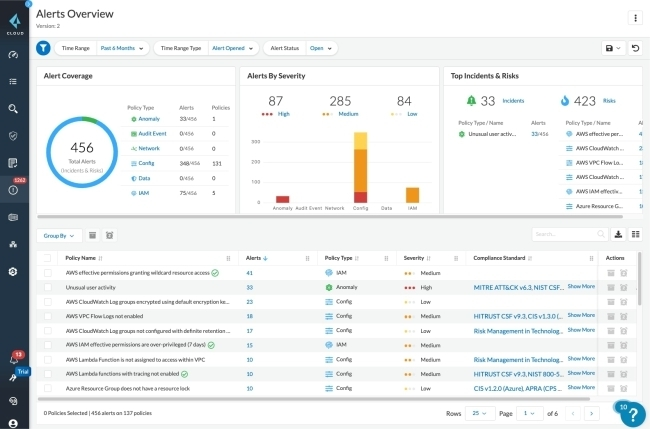
Palo Alto Networks Prisma Cloud, formerly known as RedLock, specializes in security and compliance monitoring for AWS. It provides visibility into cloud resources, monitors network traffic, and identifies potential security risks.
Pros:
- Offers comprehensive security and compliance monitoring.
- Provides valuable visibility into AWS resources and network traffic.
- Helps organizations maintain a secure and compliant AWS environment.
Cons:
- Pricing may not be suitable for smaller businesses.
- Advanced features may require additional configuration and expertise.
Pricing: Palo Alto Networks Prisma Cloud pricing is available on request and typically depends on the specific needs of the organization.
14. McAfee MVISION Cloud
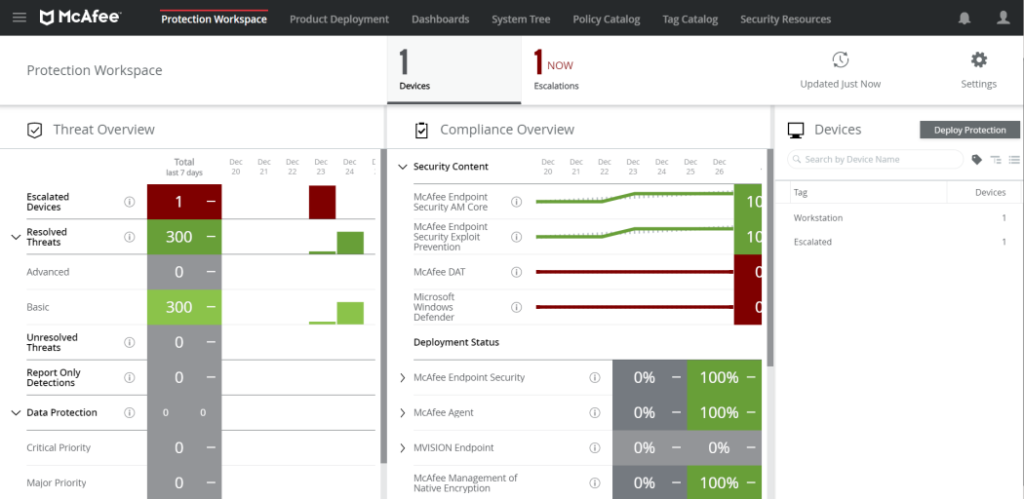
McAfee MVISION Cloud is a cloud-native security platform focused on safeguarding data and applications within AWS. It offers features such as data loss prevention, threat protection, and policy enforcement.
Pros:
- Strong data protection through data loss prevention (DLP) capabilities.
- Effective threat protection for cloud-based assets.
- Enables policy enforcement to maintain security standards.
Cons:
- Pricing can be on the higher end for certain organizations.
- May require some configuration for optimal effectiveness.
Pricing: McAfee MVISION Cloud pricing varies based on the selected features and deployment options. Specific pricing details can be obtained from McAfee.
15. Symantec CloudSOC
Symantec CloudSOC is one of the best tools for cloud security. It specializes in providing cloud security for AWS, offering capabilities like threat detection, data protection, and cloud access security broker (CASB) features to secure cloud deployments.
Pros:
- Effective threat detection and data protection.
- Cloud access security broker (CASB) capabilities for control and visibility.
- Helps organizations secure their AWS cloud deployments comprehensively.
Cons:
- Pricing may not be suitable for smaller businesses.
- Implementation and configuration may require expertise.
Pricing: Symantec CloudSOC pricing is available on request and typically depends on the specific requirements and deployment size of the organization.
Types of Cloud Security Tools
There are several types of cloud security tools available to protect cloud-based resources and data. Some of the most common types of cloud security tools include:
- Intrusion Detection and Prevention Systems (IDPS): IDPS are systems that monitor network traffic for signs of unauthorized access or malicious activity. They can alert security personnel to potential security threats and take action to block the activity.
- Access Control: Access control tools are used to manage user access to cloud-based resources. They can control who has access to specific resources, what actions users can perform, and when they can perform those actions.
- Identity and Access Management (IAM): IAM tools are used to manage user identities and access to cloud-based resources. They can authenticate users, manage user permissions, and provide single sign-on (SSO) capabilities.
- Cloud Security Information and Event Management (CSIEM): CSIEM tools are used to monitor and analyze security-related data from various sources, including cloud-based resources. They can provide real-time visibility into security events and alert security personnel to potential security threats.
- Cloud Security Orchestration, Automation, and Response (SOAR): SOAR tools are used to automate security processes and respond to security incidents. They can integrate with other cloud governance security tools to provide a comprehensive security solution.
- Cloud Security Posture Management (CSPM): CSPM tools are used to assess the security posture of cloud-based resources and provide recommendations for improvement. They can help organizations comply with regulatory requirements and industry standards.
Cloud Security Trends
In comparison to the traditional way, the importance of cloud security infrastructure appears more practical and dependable according to the new cloud security assessment tools. The cloud environment can be protected from data breaches by having a good security plan in place and by keeping an eye out for emerging trends; like zero trust, hybrid environment, DevSecOps, cybersecurity mesh etc., in AWS cloud security.
An organization has the option of migrating all of its data to the cloud or just some of it, with other cloud security audit tools and services being privately hosted. Since using a hybrid strategy is more secure than shifting everything to the cloud, most businesses opt to employ it.
With the right cloud based security tools, you can block internal threats, automate security,, and lower the risks of breach.
Best Practices for Implementing Cloud Security Tools
To avoid security issues in cloud computing, review all risks and duties with every employee who has a cloud account when applying the best cloud security management tools and standards. Hackers will get access to the cloud environment more readily if your personnel lack the skills to recognize cyber dangers like scam emails or malware attacks.
Using the cloud network to transfer data will increase the chance of exposure but the following measures will help secure the data;
- Data encryption
- Monitoring system setup
- Understanding risks and responsibilities
- Employee training

Protect Your Business with Custom Cloud Security Solutions
Our custom cloud security solutions are designed to keep your business protected from cyber threats. Contact us today to learn how we can secure your data and systems in the cloud.
Conclusion
Implement stringent access controls and make sure that only those who truly require access are given access to prevent unwanted access to your data.
Data and applications will always be accessible to authorized users at the appropriate moment thanks to cloud security assessment tools. Therefore, you need a trustworthy way to access cloud applications and data so that you can address any potential security issues.
- Frequently Asked Questions
Q1. Why do DevOps need cloud security solutions?
In cloud security management, DevOps is very important. It helps companies in ensuring the security and industry compliance of their applications and services. DevOps aids businesses in locating and fixing security flaws in their services and apps.
Q2. What are the three types of cloud computing?
The three types of Cloud Computing are:
- IaaS – Infrastructure as a Service
- PaaS – Platform as a Service
- SaaS – Software as a Service
Q3. What is cloud security software?
Cloud security, also known as cloud computing security, is a set of measures for security controls developed to safeguard data, apps , and infrastructure stored in the cloud. These protocols help ensure the data privacy and protection, user and device authorization, and access management of the resources and data.