Understanding what Azure is and how to use it effectively has become essential for businesses looking to modernize their operations without falling into common technical traps. As Microsoft’s cloud computing platform, Azure supports everything from virtual machines to advanced DevOps workflows, but simply adopting the technology isn’t enough. Missteps in configuration, workflow management, and tool selection can lead to wasted resources and unstable deployments.
In fact, according to Gartner, over 85% of organizations will adopt a cloud computing strategy by 2025, indicating a significant shift towards cloud platforms like Azure. Why? While Azure offers powerful capabilities, success often depends on following Azure DevOps best practices, selecting the right tools, and avoiding costly errors that stall development or lead to outages.
This guide breaks down what Azure is, explores the best practices for Azure DevOps, highlights tools worth considering, and calls out common mistakes to watch for. Whether you’re new to Azure or refining your cloud strategy, knowing the right way to approach DevOps in this environment makes all the difference.
Azure DevOps Best Practices
Using Azure DevOps effectively goes beyond writing code and pushing it to production. It involves structured planning, strong collaboration, and a consistent workflow that aligns with business goals. Below are some time-tested Azure DevOps best practices that ensure smoother operations, fewer deployment failures, and greater team efficiency.
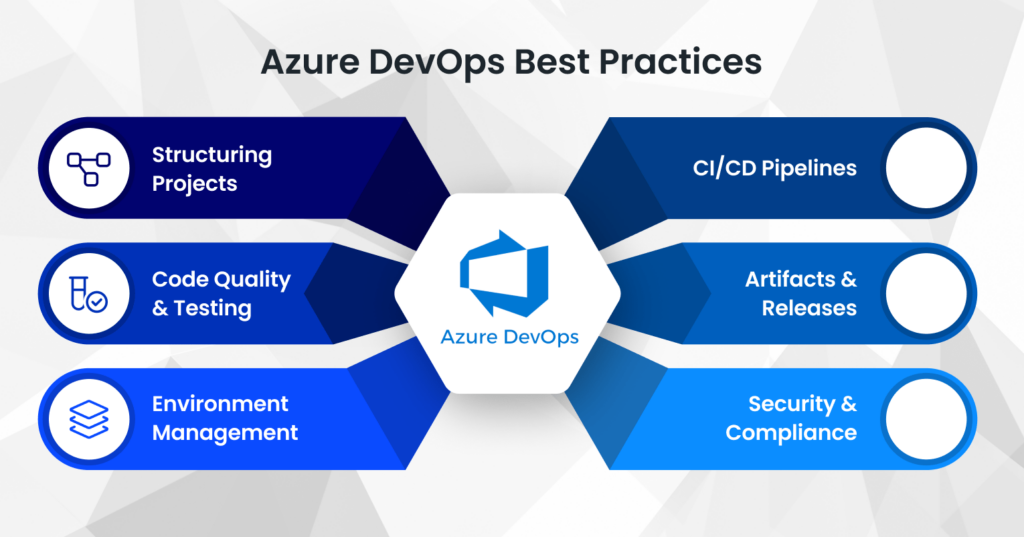
Setting Up for Success – Structuring Azure DevOps Projects for Long-Term Success
The foundation must be right before any pipelines or code repositories come into play. One of the most common mistakes teams make is diving into Azure DevOps without properly structuring their projects, repositories, and permissions. This can lead to scattered resources and a lack of accountability.
Start by clearly defining your Azure DevOps organization and project structure. Use a naming convention that reflects your team hierarchy and environment stage. Configure roles and access rights carefully—the principle of least privilege is key here.
Teams often forget that inappropriate access controls can lead to unauthorized changes or security gaps. Forrester has highlighted the significance of securing applications and integrating security into DevOps practices.
Key setup actions:
- Define repository strategy (mono-repo vs. multi-repo).
- Configure branching policies and role-based access control (RBAC).
- Set clear responsibilities using Azure Boards.
Building Smart Pipelines for CI/CD in Azure DevOps
Your build and release pipelines are the engines of your delivery process. Poor pipeline design leads to failed deployments, longer build times, and inconsistent results.
One best practice for Azure DevOps pipeline design is modularization. Break your pipeline into build, test, artifact creation, and deployment stages. This makes troubleshooting easier and reduces the blast radius if something breaks.
Another overlooked tactic is the use of YAML templates. Templates help you avoid repetition, ensure consistency, and make the pipeline easier to maintain. YAML-based pipelines, introduced as a replacement for Classic pipelines, also support version control, an essential win for traceability.
DevOps consulting services can aid in designing and optimizing these pipelines, tailoring them to your team’s unique needs and goals. This approach helps enable faster, more reliable delivery while reducing operational bottlenecks.
Timeout settings, retry logic, and conditional triggers must also be configured carefully. For example, don’t trigger a deployment to production on every code push—use manual approvals and environment gates.
Key tips:
- Use YAML for source-controlled pipeline definitions.
- Include pre-deployment approvals for critical stages.
- Avoid hardcoding values—use variables and parameterization.
- Run builds in parallel where possible to reduce waiting time.
Code Quality and Testing in Azure DevOps Workflows
Code quality cannot be an afterthought. Teams often treat testing as a checkbox, rather than an integral part of the CI/CD lifecycle. Start by enforcing branch protection rules, including mandatory code reviews, status checks, and build validation before a pull request can be merged.
As organizations modernize cloud design, embedding quality controls directly into the pipeline becomes essential. Tools like SonarCloud, ESLint, and StyleCop can be integrated into the build process to catch issues early. Unit testing is only one part of the picture. Use integration tests, smoke tests, and UI automation wherever applicable. Set thresholds for code coverage, but don’t just chase high percentages—focus on testing logic-heavy and high-risk areas.
Here’s where best practices for Azure DevOps shine: schedule test suites to run automatically on pull request validation and merge to main branches. This guards against introducing regressions.
To keep pipelines fast:
- Split tests into fast unit tests and slower functional tests.
- Use test impact analysis to only rerun tests affected by recent code changes.
- Store test results and logs as artifacts for post-build review.
Managing Artifacts and Releases – From Build to Production the Right Way
Every successful deployment relies on reliable and traceable artifacts. An artifact is any file or bundle created during a build, such as a compiled DLL, container image, or deployment package.
With Azure DevOps, Azure Artifacts can host and manage packages (NuGet, npm, Maven, etc.). This provides a controlled environment where you can share versioned components across projects. Tag your artifacts with version numbers and metadata. Avoid mutable builds. Once an artifact is created and tested, it should never be rebuilt. Instead, promote that exact artifact through testing and production stages.
Automate your release pipelines using Release Pipelines or multi-stage YAML pipelines. Clearly separate build from deploy stages to avoid coupling. You can also use deployment rings—start with internal testers, then gradually expand to the full user base. Whether you’re using Azure or aiming for AWS DevOps mastery, applying these principles ensures consistent, repeatable, and secure deployments across environments.
Artifact tips:
- Enable artifact retention policies to clean up old packages.
- Use semantic versioning for clarity.
- Log every release with links to commits, build IDs, and approval history.
Environment Management to Handle Multi-Stage Deployments Effectively
One of the trickiest areas is managing development, testing, staging, and production environments. These may have slightly different configurations, leading to the notorious “it works on my machine” problem.
Use Azure Resource Manager (ARM) templates, Terraform, or Bicep to provision infrastructure as code. This allows you to replicate environments consistently across stages. Name and tag resources based on environment, purpose, and owner. It makes cost tracking and resource cleanup more manageable.
Introduce environment-specific variables in your pipelines rather than duplicating pipeline definitions. To manage this cleanly, use Azure DevOps’ built-in environment and variable group features.
Environment handling suggestions:
- Set up approval workflows between environments.
- Use deployment slots for zero-downtime deployments.
- Tag resources with metadata (owner, cost center, environment).
- Automate resource cleanup for temporary testing environments.
Securing DevOps for Compliance, Secrets, and Audit Trails
Security is often bolted on late in the process, which is risky and inefficient. Instead, embed security from the start, a concept often called “shift-left” security.
When considering Azure security vs AWS security, Azure offers native integrations like Microsoft Defender for DevOps, making it easier to embed security directly into CI/CD pipelines. Tools like WhiteSource Bolt or OWASP ZAP can be integrated to identify code, container, and dependency vulnerabilities before they reach production—similar to options available on AWS, but with tighter integration in Microsoft environments.
Set up audit trails and enable logging for sensitive operations. Rotate secrets regularly and never store them in plain text. Store secrets in Azure Key Vault and reference them securely from your pipelines.
Best practices for secure pipelines:
- Use service connections with the least privileges.
- Scan dependencies regularly for vulnerabilities.
- Encrypt sensitive values using secure variables or Key Vault.
- Conduct regular security reviews of pipeline configurations.
Common Mistakes to Avoid in Azure DevOps
While Azure DevOps offers a powerful suite of tools for managing development workflows, it’s surprisingly easy to fall into practices that hinder productivity, compromise security, or introduce inefficiencies. Understanding what not to do is just as important as following Azure DevOps best practices. This is where the role of a DevOps consultant becomes crucial—helping organizations identify these pitfalls early and build efficient, secure, and scalable workflows. Below are some of the most common mistakes teams make—and how to avoid them.

1. Poor Repository Management
One of the foundational errors in Azure DevOps is mismanaging source control. This includes having too many loosely defined repositories, inconsistent naming conventions, or worse, storing sensitive data (like credentials) in the repo.
Why it matters: Poor repository structure leads to confusion, reduced collaboration, and security risks.
Avoid it by:
- Establishing clear naming conventions.
- Using .gitignore to avoid committing unnecessary files.
- Scanning for secrets with tools like GitGuardian or Azure’s built-in credential scanners.
2. Overcomplicated CI/CD Pipelines
Some teams create sprawling pipelines with unnecessary tasks, poor modularity, and redundant steps. This not only slows down deployment but also makes debugging much harder.
Why it matters: Complex pipelines are hard to maintain, test, and scale. Teams that invest in CI/CD consulting often streamline these processes by identifying inefficiencies and introducing industry best practices.
Avoid it by:
- Using YAML templates to reuse components.
- Keeping steps atomic and readable.
- Separating build and release stages.
- Implementing pipeline linting or validation before commits.
3. Neglecting Branch Policies
Teams sometimes skip enforcing branch protection rules, which leads to unreviewed code being merged into main branches.
Why it matters: This can introduce bugs, security flaws, and break builds in production—especially in environments driven by Cloud and AI, where automation and scalability amplify the impact of bad code.
Avoid it by:
- Requiring pull requests (PRs) for all merges to protected branches.
- Setting mandatory code reviews and status checks.
- Enforcing build validations for key branches.
4. Inconsistent or Missing Testing Practices
Skipping automated testing is a major DevOps misstep. Even worse is inconsistent implementation—some modules have tests while others don’t.
Why it matters: Lack of testing leads to unpredictable code behavior and delayed bug detection.
Avoid it by:
- Integrating unit, integration, and regression tests into the pipeline.
- Setting minimum code coverage thresholds.
- Using tools like Azure Test Plans or third-party integrations (e.g., NUnit, Selenium).
5. Poorly Managed Environments
Deploying directly to production without proper staging or QA environments is a recipe for disaster. Teams also sometimes reuse secrets and configurations across environments, which increases the risk of exposure or misconfiguration.
Why it matters: It jeopardizes application stability and security.
Avoid it by:
- Clearly defining development, staging, and production environments.
- Using environment-specific configurations and variable groups.
- Isolating credentials via Azure Key Vault and linking securely to pipelines.
6. Ignoring Role-Based Access Controls (RBAC)
Giving all users blanket access to repositories, pipelines, or environments leads to accidental misconfiguration or even internal security breaches.
Why it matters: Mismanaged permissions are among the top contributors to DevOps-related security incidents. Organizations leveraging cloud consulting services often uncover these oversights during audits or security reviews.
Avoid it by:
- Using Azure Active Directory (AAD) for identity management.
- Assigning roles based on the principle of least privilege.
- Regularly auditing user roles and access levels.
7. Lack of Monitoring and Feedback Loops
Once code is deployed, some teams fail to implement continuous monitoring, logging, or feedback collection.
Why it matters: Without insight into performance or user issues, bugs go unnoticed and user satisfaction declines.
Avoid it by:
- Integrating Azure Monitor and Application Insights.
- Setting up alerting for deployment failures or abnormal metrics.
- Creating feedback loops with stakeholders for iteration.
8. Skipping Documentation
It’s tempting to rely on tribal knowledge or “it’s in the pipeline,” but undocumented processes create bottlenecks, especially as teams scale.
Why it matters: Without clear documentation, onboarding new team members or debugging issues becomes slow and error-prone.
Avoid it by:
- Documenting pipelines, workflows, permissions, and rollback strategies.
- Storing documentation in a shared, version-controlled repository.
- Making documentation part of the definition of done.
Recommended Tools and Extensions for Enhanced Azure DevOps Use
Integrating the right tools and extensions is essential to get the most out of Azure DevOps. These additions help organize and manage workflows, enforce quality standards, and increase visibility across the development lifecycle. Incorporating these tools can significantly improve efficiency, security, and collaboration across your Azure DevOps workflows.
Managed cloud services can further support these efforts by reducing operational overhead and ensuring your team can focus on delivering high-value software instead of maintaining underlying infrastructure.
Below are some of the most effective and widely adopted tools for Azure DevOps teams.
1. Azure DevOps Extension Marketplace
Start with the official Azure DevOps Marketplace. It offers thousands of free and paid extensions that integrate directly into your pipelines, boards, repos, and more.
2. SonarQube
For teams focused on maintaining high code quality, SonarQube is a leading tool for static code analysis. It integrates easily with Azure Pipelines and helps catch bugs, vulnerabilities, and code smells before they reach production.
3. Terraform and Azure DevOps Integration
Infrastructure as Code (IaC) is vital for managing cloud environments. Terraform’s Azure DevOps extension simplifies provisioning and managing infrastructure using consistent, repeatable code.
4. WhiteSource Bolt (now Mend Bolt)
Security is critical in DevOps. Mend Bolt scans open-source dependencies for vulnerabilities and license issues within Azure Repos and Pipelines.
5. Azure Key Vault
This is more than a tool, it’s a must-have for managing secrets securely. Integrating Azure Key Vault with your pipelines ensures that tokens, passwords, and certificates are not exposed in logs or code.
6. Slack or Microsoft Teams Integration
Keeping your team in the loop is easier with messaging integrations. Set up pipeline notifications or PR updates directly in Slack or Teams to promote real-time collaboration.
FAQs
Can you name three best practices in Azure DevOps?
Use infrastructure as code (IaC), implement CI/CD pipelines, and integrate automated testing.
What are DevOps best practices?
Key DevOps best practices include continuous integration, continuous delivery, infrastructure as code, and ongoing monitoring.
What are the 5 components of Azure DevOps?
Azure Boards, Azure Repos, Azure Pipelines, Azure Test Plans, and Azure Artifacts.
What are the three main features of Azure DevOps?
Version control with Azure Repos, CI/CD with Azure Pipelines, and agile planning with Azure Boards.
What are the 3 pillars of Azure?
Compute, Storage, and Networking.
What are the 4 key components of DevOps?
Culture, Automation, Measurement, and Sharing (CAMS).
Conclusion
Mastering Azure DevOps goes far beyond setup — it’s about establishing best practices, avoiding common pitfalls, and using the right tools to organize and manage workflows. With businesses increasingly shifting to cloud platforms like Azure, understanding how to structure your DevOps environment, secure your pipeline, and maintain code quality is vital. Folio3 cloud services can be a powerful partner in this process. Our team of cloud services experts helps you implement and customize your Azure DevOps platform to align with your unique business needs. From designing scalable pipeline strategies and integrating automated testing, to strengthening RBAC controls and securing secrets, Folio3 guides you through each step. We enable your team to maximize the capabilities of Azure DevOps — ensuring faster releases, higher code quality, and a more resilient, efficient, and compliant delivery lifecycle in the Azure ecosystem.